Description
10.13.37.21:1337
https://dctf.def.camp/quals-2016/exp100.bin
Exploit
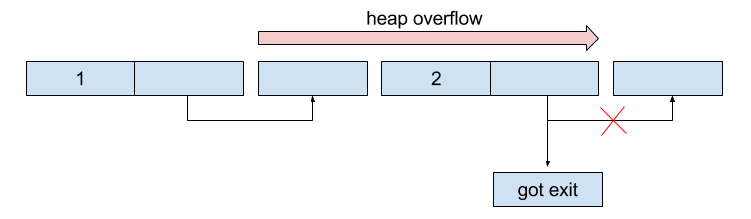
The binary malloc four chunks as the figure shown above. The first and the third chunks contain a pointer to the second and the fourth chunks respectively. Then, it will invoke two fgets to these two pointers. We can make use of the buffer overflow bug of the first fgets to change the destination of the second fgets. By changing the value of the GOT of exit to the embedded print-flag function, we can get the flag easily.
1 | from pwn import * |
Flag:
DCTF{b94c21ff7531cba35a498cb074918b3e}